What is Malware?
Malware is quite a large term, encompassing most internet threats such as viruses, worms, trojan horses, adware, and spyware. Before delving deeper into the topic of malware, you should be aware that malware differs from types of online internet threats as it is actually an abbreviation for "malicious software". In the United States, some legal codes define malware as a "computer contaminant", or something which infects your desktop or browsing device. By understanding malware is software, which means it must be downloaded or actively added to your computer, browser, or downloaded from a USB stick, you can take the first step to personal, vigilant protection.
Non-virus types of Malware:
Adware
The most common type of malware is adware, which can be from legitimate companies (for marketing or purposes) or sole perpetrators (for thievery). Adware is designed in order to force advertisements upon you while using your computer. Adware can also not just force advertisements and slow down your computer experience, it can also place hidden trackers, cookies, or retargeting pixels on your browser. By doing so, the owners of said adware can track your movements online and provide even more advertisements based on your browsing history. The more ads appearing on your computer, the slower your computer will run as disk space is taken up and the more likely your data will be mined. Adware can also contain hidden spyware, which we will cover next.

Spyware
Spyware is pretty self-explanatory via the name, but anyways, it is a malicious computer software which scans your computer’s hard-drive and browser history for personal information and internet habits. Essentially, yes, spying on you. Spyware can uncover a lot of information on your computer, including email passwords and usernames, logins for social media, your age, or gender, as well as sensitive financial information. The worst of spyware can actually alter your computer settings as well, decreasing your computer’s efficiency.
Trojan Horse
Last, but certainly not least, there is the Trojan horse of malware. And yes, its name comes from the story of the Trojan horse - why? Because it acts in the same way as in the story. A trojan horse appears as a program which has useful features. The trick? It does not - it actually contains pieces of damaging code which can give the malware the ability to rewrite code or alter code within your computer. A Trojan horse differs from a virus or a worm as it does not replicate itself; however, many worms or viruses use the tactics of a Trojan horse to initially infect a system.
Breakdown: Virus side of Malware
Virus
A virus is another form of malware, which like spyware, once again finds its meaning in its name. A virus is similar to a medical virus, i.e., it infects your system, taking up disk space, altering code, and deleting or corrupting files on your computer. Viruses are usually hidden quite well in the forms of emails, attachments, shared files, images, or games. A virus can be tricky to get rid of without the help of a legitimate security system as they can secretly affect your hard-drive, all while appearing as a legitimate application.
Worms
A worm acts in a similar way as a virus in the sense that it replicates itself within an infected system. However, a worm goes one step beyond a virus (not in lethality, but in the capability of spreading) by duplicating itself over and over again. Once again, filling up your memory space or overloading your computer’s processing speed to slow down your system entirely. The worst part about worms is that they are self-sustaining, meaning the creator or owner of the malware does not spread the worm. Instead, the worm spreads itself by infecting your messaging systems, web browser, emails, or social media and sustains its own duplication and diffusion rates across the internet.
How to protect yourself from Malware?
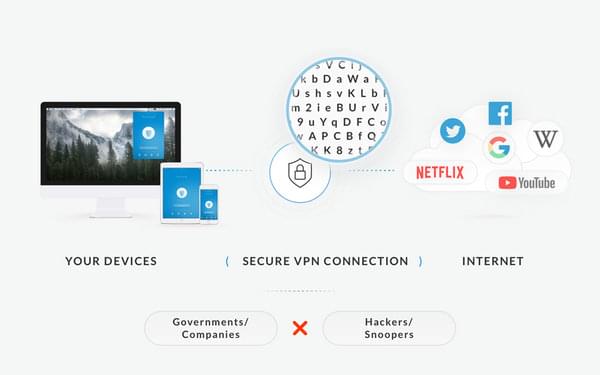
In order to protect yourself from these dangerous, hidden threats, you must be aware of when and how they infect your system. So, take precaution when opening strange emails, spam, sketchy websites, downloads, etc. this is the first step to protection. The second step is to have an anti-virus, secure-email product, or for adware in specifics, an ad blocker. The only way to stay secure and safe from any kind of Malware is to own an Anti-Virus and a reliable VPN. ZenMate VPN does not only offer anonymity online, it also encrypts all your data and detects sites with malicious content.
Download ZenMate VPN in 3 Simple Steps
ZenMate VPN offers the best solution for preventing malware. Not only does ZenMate secure your online privacy, it also makes sure that your internet activity is always safe. To download, set-up and surf anonymously with ZenMate is super easy:
1. Download Zenmate's browser extension, desktop client or mobile app by clicking on PRODUCTS and choosing your platform.
2. Follow the instructions within your VPN app or client in order to create your ZenMate account.
3. Choose which server location you would like to connect to and then click the big round button - your IP is now completely hidden and your device safe from malware.
Why is ZenMate VPN a must?
Overall, ZenMate is the best choice for anyone looking to hide their IP address, unblock online content, and stay anonymous online. ZenMate is a globally trusted VPN service with over 42 million users worldwide. We have servers based in over 77 locations, including the US and UK, meaning you can choose from a wide variety of countries when changing the location you would like to access the web from and at the same time hide your IP address. Finally, ZenMate vows to never keep any log of your browsing data. As a German company, we are bound by strict data privacy laws which ban us from selling your information, even if we wanted to. We are committed to offering our users a private, secure and unrestricted web.