What is Encryption?
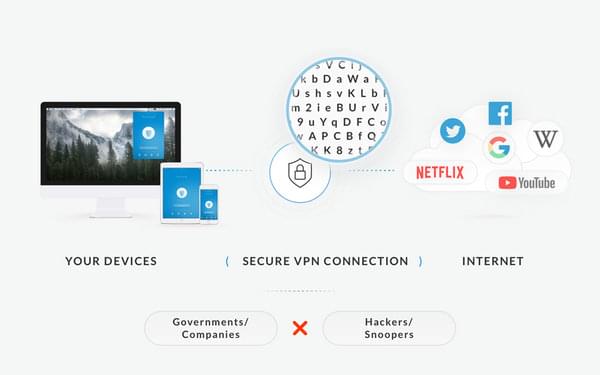
As the internet is becoming more and more advanced, it is also becoming much more dangerous. Private browsing is ceasing to exists and now the only way to ensure security and privacy online is with a reliable VPN. A VPN does not only hide your IP and unblock all of your favorite content, it also provides data encryption. Data encryption disguises the data we share online into tiny bits, so nobody unauthorized can gain access to it unless they have a key to open it.
Encryption uses mathematical functions like algorithms to secure online data and can be used to secure anything from plain text to a whole operating system. Even though it is very big part of the online world, many people are unaware of it and that it comes in different sizes and shapes. Read on to find out more about what encryption is and learn how to distinguish the main differences between the most famous 128-bit and 256-bit types of encryption.
To understand the difference between 128-bit encryption and 256-bit encryption, it is important to know the basics of this online security method. Encryption is a process that uses an algorithm in order to transform information to make it unreadable. If someone wishes to decrypt the text and read it, then they have to make it readable with a key. This security process is almost the same as a receiving a letter in your name and not being able to open the envelope without the opener.
A deeper look into Encryption
We live in a world where security breaches are occurring every single day that is why it is important to be aware how you can protect yourself and what ways are there achieve the protection. There are more 3 main types of encryption and each type has its own benefits and specific aspects of keeping you secure from cybercrime.
Symmetric encryption: In essence, symmetric encryption entails a method of encryption which encrypts and decrypts information (data) with a symmetric key - i.e. the same key is used to decrypt and encrypt. The information is scrambled in order to prevent anyone from accessing, reading, and understanding information stored online or on an encrypted disk. This method of encryption is quite fast, but when an exchange of information happens through this type of encryption, both parties participating needs to have the same key in order to decrypt the information
Asymmetric encryption: Asymmetric encryption works in a very similar way, as it essentially encrypts all data. The difference, however, is that asymmetric encryption uses two different keys to encrypt and decrypt said data. This means that if someone has access to the first key, named the public key, a private key is needed to decryp
Hashing: Hashing is also considered to be a type of encryption as it uses cryptography. The name comes from the fact that it takes a piece of data, encrypts the data with a key, hashes the data with different techniques such as SHA-3, then encrypts the given key. Once this is done, the public key becomes unreadable and signifies that the message entailed hasn’t been modified before encryption. Finally, the hash data is signed with the recipients (i.e. the person who will access the encrypted data) with a private key. Most commonly, this technique is used to protect passwords as it gives a strong indication of integrity and consistent data
The importance of keys in Encryption
Keys are one of the most important, if not most important, part of encryption as it provides the ability to view the said data. An encryption key is a line of text or symbols created out of bits in order to encrypt and decrypt data. All keys are created with the help of algorithms. Keep in mind that the longer the key is, the harder it will be to crack. This is where the different numbers come into play of encryption. 128-bit encryption has a shorter key than 256-bit encryption, which is shorter than 1028, and so on and so on. In simpler words, a key is a password.
An introduction to 128-bit Encryption
128-bit encryption is a technique used to encrypt and/or decrypt data or files by using a 128-bit key to achieve that. It is considered to be one of the most secure and most popular online security methods. Interesting fact, 128-bit encryption is considered to be logically unbreakable, so you could say that 128-bit security is top notch!
128 bit, encryption, keys - all that might sound complicated and not easy to understand, but trust us when we say that we can make it simple. The 128 number refers to the length of the encryption or decryption key and the reason why it is considered to be one of the most secure is that it would take an immense amount of time to crack the key open. The key is built out of a mathematical algorithm and even a genius, robot or a super powerful computer would not be able to find the right combination of numbers to open it. This type of online security is so good, that most network and internet connections, as well as web browsers, are using this type of security.
256-bit encryption is a technique that uses a 256-bit key to encrypt and/or decrypt data and files. It is considered to be just as secure as a 128-bit method and most often it is used in modern technologies. 256 refers to the length of the encryption key, meaning that there are 2256 combinations to break the encrypted information. To put it simply, even the most powerful computers are usually unable to break 256-bit encryption. Most commonly, this type of online security is being used for data in transit. Interesting fact, the US government requires all its data to be encrypted using 256-bit methods, so that should give you an idea how secure 256-bit technique is!
128-bit vs. 256-bit Encryption - which one is better?
The main difference between the two different types of encryption is the size. And in this case, the bigger the size does not mean that the product is better at functioning. The 256-bit encryption method is longer and thus might take more time to decrypt, hence some people assume that it provides stronger security. In other words, the longer the key, the more effective security. However, that is not necessarily true, as the length of the key makes the 256-bit encryption slower, hence not as complex as 128-bit type.
Just to make it clear, both methods of security are strong and do what they are supposed to do - encrypt data. One of the main differences is that the 128 bit is more common amongst everyday people, while 256-bit encryption is mostly used for large corporations, sensitive financial firms, and government standards.
Setup ZenMate VPN in an instant!
To download, set-up and start encrypting your data with ZenMate is super easy:
1. Download Zenmate's browser extension, desktop client or mobile app by clicking on PRODUCTS.
2. Follow the instructions within your VPN app or client in order to create your Zenmate account.
3. Choose which server location you would like to connect to and then click the big round button - your data is now encrypted.
Is ZenMate VPN the best choice for encrypting my data?
ZenMate VPN is a trusted and reliable VPN service provider located in Berlin, Germany. With more than 42 million downloads and still growing, ZenMate offers hundreds of servers in 77+ locations, turbo speeds, and top-notch encryption. We are committed to helping create a more secure, private and free internet for all.